As we continue to use CrowdStrike Falcon Complete for protecting critical assets, it’s important for us to recognize the difference between Detections and Incidents in the Falcon interface. Both terms are critical in maintaining the security of our systems, but more importantly, differentiating the levels of concern and action needed when each is presented. Here’s a breakdown of what each means, with examples and guidance on how to plan a response:
Detections: First Line of Defense
What is it?
A detection refers to Falcon identifying and alerting you to a potentially malicious activity or suspicious behavior. Detections are often based on known attack patterns, behaviors, or indicators of compromise (IOCs).
Example of Detection:
A detection could occur when Falcon identifies a suspicious process, such as a PowerShell script executing in a way that matches a known malicious behavior (e.g., PowerShell being used to download a remote access application instead of this being performed by using a web browser). Falcon could flag this as a detection for review.
In Falcon Complete, many detections are automatically handled (blocked or quarantined), but it’s useful to monitor these and ensure these detections and actions are meeting your expectations.
How to react:
- Verify actions taken by the Flacon Platform are appropriate for your environment.
Incidents: Escalated Threats
What is it?
An incident refers to a confirmed or suspected compromise. Incidents are usually escalated detections, where Falcon Complete has grouped multiple related detections into a broader security event that requires investigation.
Example of Incident:
An incident might be triggered when several detections, such as an unauthorized PowerShell execution, network traffic to a known malicious IP, and an attempt to modify system files, are correlated. This indicates a more serious compromise or advanced attack, such as a ransomware attack or persistent threat. In these situations, you will likely want to be notified and quickly alerted as opposed to periodically checking these alerts.
How to react:
- Immediate action required: Incidents are a higher priority and require you to take immediate steps. Falcon Complete will typically provide a recommendation on how to respond (e.g., isolate the affected machine, investigate further, or apply specific mitigation steps).
- Cooperation with Falcon Complete: In many of these situations, Falcon Complete will take automated remediation steps. If that happens, follow up with any additional actions they recommend, like reviewing logs or monitoring the system after isolation.
Consistency Across Falcon Modules
It’s important to note that incidents and detections may not be consistently named across all Falcon modules. For example, while Falcon Complete uses both terms, other modules (like Falcon Insight or Falcon Prevent) might focus solely on detections, as these modules are more geared toward alerting and blocking threats at earlier stages. However, the principles remain the same:
- Detections: Indications of suspicious behavior.
- Incidents: Escalated events requiring broader attention.
Comparison Example:
Imagine you log into your cloud email provider’s security dashboard and see phishing emails entering your domain, yet being blocked from going to your users’ inboxes. This is a detection. It’s useful to understand and know what happened, but no action is really needed for this specific security event.
In that same scenario, imagine the first few emails were delivered to inboxes, your users followed a link in the email, credentials were entered at a malicious webpage and now those credentials are being used to access other systems. This security event has now been elevated to an incident and will very likely require action. This now becomes an involved event which requires resources, time and remediation.
What do all the symbols and colors mean?
On Image 1, you will notice colorization of severity but with slight icon variation for certain detections. Across the Crowdstrike Platform you’ll regularly see variations. Images 2 and 3 are the legends Crowdstrike has made available describing each of the symbols.
These can also be found at the following URL:
https://falcon.us-2.crowdstrike.com/documentation/page/nec99068/endpoint-detection-monitoring
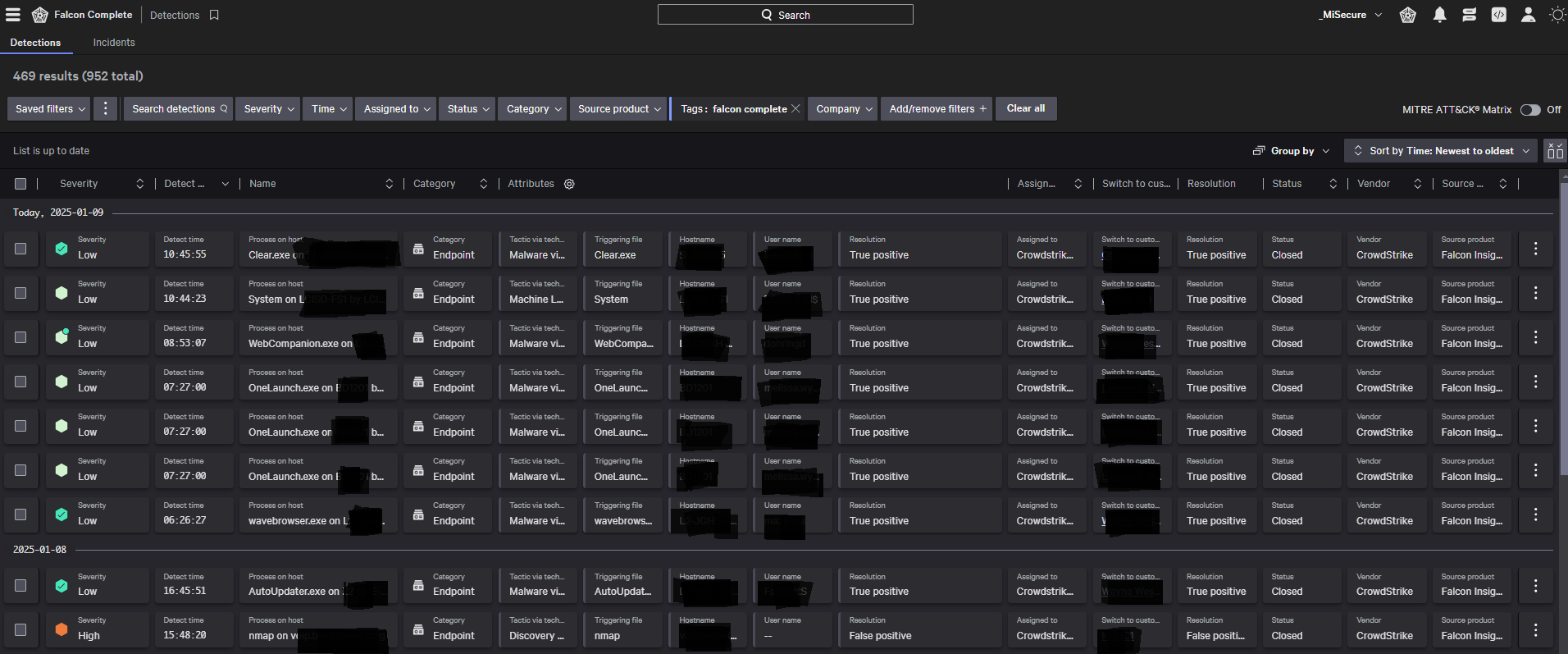
Image 1
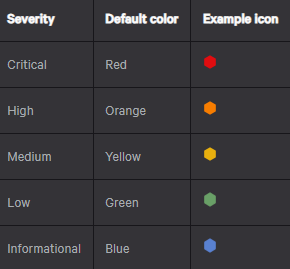
Image 2
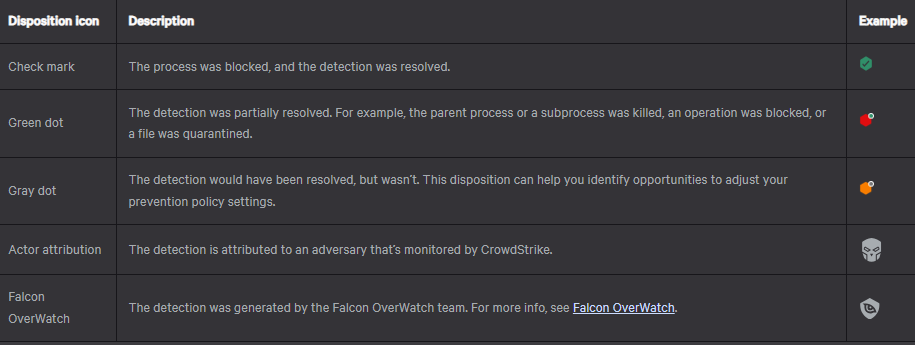
Image 3